| 1 |
DENIED
|
ROLE_USER
|
null |
|
Show voter details
|
| 2 |
DENIED
|
moderate
|
Proxies\__CG__\App\Entity\Entry {#2452
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "WORKAROUND-Nextcloud-portforward-stops-working-when-it-is-moved-to"
+title: "[WORKAROUND] Nextcloud portforward stops working when it is moved to a bridged network"
+url: null
+body: """
cross-posted to: [sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)\n
\n
---\n
\n
I have the following topology:\n
\n
\n
\n
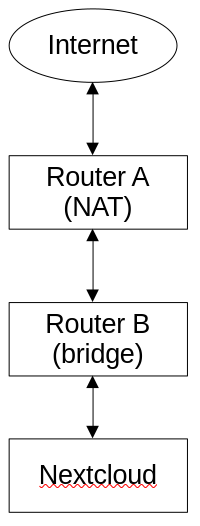
The device running Nextcloud (snap) used to be connected to Router A, but I have recently added a bridge (Router B) and I moved Nextcloud’s device to that bridged network; however, as soon as Nextcloud was moved to Router B, the portforward on Router A seemed to stop working – as in I cannot connect to nexcloud from the public IP anymore. Bridges operate at layer 2, so this *should* make no difference whatsoever (this is reflected in the fact that other services (like SSH) still work perfectly fine portforwarded – it’s only Nextcloud that doesn’t work), which leads me to think that it is a Layer 7 (i.e. Nextcloud) issue. What’s going on here? How can Nextcloud even tell that it’s been placed on a bridged network?\n
\n
**EDIT (2024-01-16T00:19Z):**\n
\n
I performed a network capture on the device running Nextcloud, and it appears that it’s receiving the incoming request (`SYN`), and responds appropriately (`SYN, ACK`), but then Router B responds with `Destination unreachable (Network unreachable)`, which is then, of course, followed by many requests for retransmission as the packets are being dropped. But what’s causing the packets to be dropped? Why aren’t they making it through the network?\n
\n
**EDIT (2024-01-25T08:37Z):**\n
\n
I’m not 100% sure what the previous problem was, but I think that it had to do with [the bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that I was using – not necessarily that it was broken, but perhaps it was jsut incompatible with the setup in some way. What I ended up doing was buying [a different router that supported WDS](https://web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/E8450-CA.html), and then I created a WDS bridge between the two routers. The network seems to be working reliably, and as expected now.
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 4
+favouriteCount: 21
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1728530527 {#2364
date: 2024-10-10 05:22:07.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1909 …}
+votes: Doctrine\ORM\PersistentCollection {#1410 …}
+reports: Doctrine\ORM\PersistentCollection {#1907 …}
+favourites: Doctrine\ORM\PersistentCollection {#1407 …}
+notifications: Doctrine\ORM\PersistentCollection {#2391 …}
+badges: Doctrine\ORM\PersistentCollection {#2369 …}
+children: [
App\Entity\EntryComment {#1611
+user: App\Entity\User {#260 …}
+entry: Proxies\__CG__\App\Entity\Entry {#2452 …2}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+parent: Proxies\__CG__\App\Entity\EntryComment {#1722 …}
+root: Proxies\__CG__\App\Entity\EntryComment {#1721 …}
+body: "I’m not exactly sure what the previous issue was, but it appears that, possibly, [the previous bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that was in use was broken in some way. I have since switched the primary router to one that supports WDS, and created a WDS bridge between the two, and now everything is working as expected."
+lang: "en"
+isAdult: false
+favouriteCount: 1
+score: 0
+lastActive: DateTime @1706171781 {#1596
date: 2024-01-25 09:36:21.0 +01:00
}
+ip: null
+tags: null
+mentions: [
"@Kalcifer@sh.itjust.works"
"@deadbeef@lemmy.nz"
"@vegetaaaaaaa@lemmy.world"
]
+children: Doctrine\ORM\PersistentCollection {#1728 …}
+nested: Doctrine\ORM\PersistentCollection {#1730 …}
+votes: Doctrine\ORM\PersistentCollection {#1734 …}
+reports: Doctrine\ORM\PersistentCollection {#1727 …}
+favourites: Doctrine\ORM\PersistentCollection {#2457 …}
+notifications: Doctrine\ORM\PersistentCollection {#1617 …}
-id: 338798
-bodyTs: "'/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':21 'appear':13 'bridg':18,47 'broken':27 'creat':44 'everyth':53 'exact':4 'expect':57 'issu':9 'm':2 'one':39 'possibl':15 'previous':8,17 'primari':36 'router':37 'sinc':33 'support':41 'sure':5 'switch':34 'two':50 'use':25 'way':30 'wds':42,46 'web.archive.org':20 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':19 'work':55"
+ranking: 0
+commentCount: 0
+upVotes: 0
+downVotes: 0
+visibility: "visible "
+apId: "https://sh.itjust.works/comment/8020902"
+editedAt: null
+createdAt: DateTimeImmutable @1706171781 {#1555
date: 2024-01-25 09:36:21.0 +01:00
}
+"title": 338798
}
]
-id: 30810
-titleTs: "'bridg':12 'move':9 'network':13 'nextcloud':2 'portforward':3 'stop':4 'work':5 'workaround':1"
-bodyTs: "'-01':149,226 '-16':150 '-25':227 '/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':15 '/post/12856689](https://sh.itjust.works/post/12856689)':7 '/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':253 '/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':291 '100':233 '19z':152 '2':82 '2024':148,225 '37z':229 '7':124 'ack':178 'ad':32 'anymor':77 'appear':165 'appropri':176 'aren':216 'b':36,56,182 'bridg':34,45,78,145,250,298 'broken':263 'buy':282 'cannot':69 'captur':157 'caus':209 'connect':24,70 'cours':193 'creat':295 'cross':2 'cross-post':1 'destin':185 'devic':17,42,160 'differ':88,284 'doesn':111 'drop':205,214 'edit':147,224 'end':278 'even':136 'expect':312 'fact':95 'fine':104 'follow':11,194 'go':130 'howev':47 'i.e':125 'incom':171 'incompat':269 'ip':76 'issu':127 'jsut':268 'layer':81,123 'lead':115 'like':99 'm':231 'make':86,219 'mani':196 'move':39,53 'necessarili':259 'network':46,146,156,187,223,304 'nexcloud':72 'nextcloud':19,40,51,109,126,135,162 'oper':79 'packet':202,211 'perfect':103 'perform':154 'perhap':265 'place':142 'portforward':58,105 'post':3 'previous':237 'problem':238 'public':75 'receiv':169 'recent':31 'reflect':92 'reliabl':309 'request':172,197 'respond':175,183 'retransmiss':199 'router':26,35,55,60,181,285,302 'run':18,161 'seem':62,305 'servic':98 'setup':272 'sh.itjust.works':6,14 'sh.itjust.works/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':13 'sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)':5 'snap':20 'soon':49 'ssh':100 'still':101 'stop':64 'support':287 'sure':234 'syn':173,177 't00':151 't08':228 'tell':137 'think':118,242 'topolog':12 'two':301 'unreach':186,188 'use':21,257 'way':275 'wds':288,297 'web.archive.org':252,290 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':251 'web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':289 'whatsoev':89 'work':65,102,113,308"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1705428256
+visibility: "visible "
+apId: "https://sh.itjust.works/post/12856684"
+editedAt: DateTimeImmutable @1728530963 {#2471
date: 2024-10-10 05:29:23.0 +02:00
}
+createdAt: DateTimeImmutable @1705362256 {#2361
date: 2024-01-16 00:44:16.0 +01:00
}
+__isInitialized__: true
…2
} |
|
Show voter details
|
| 3 |
DENIED
|
edit
|
Proxies\__CG__\App\Entity\Entry {#2452
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "WORKAROUND-Nextcloud-portforward-stops-working-when-it-is-moved-to"
+title: "[WORKAROUND] Nextcloud portforward stops working when it is moved to a bridged network"
+url: null
+body: """
cross-posted to: [sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)\n
\n
---\n
\n
I have the following topology:\n
\n
\n
\n
The device running Nextcloud (snap) used to be connected to Router A, but I have recently added a bridge (Router B) and I moved Nextcloud’s device to that bridged network; however, as soon as Nextcloud was moved to Router B, the portforward on Router A seemed to stop working – as in I cannot connect to nexcloud from the public IP anymore. Bridges operate at layer 2, so this *should* make no difference whatsoever (this is reflected in the fact that other services (like SSH) still work perfectly fine portforwarded – it’s only Nextcloud that doesn’t work), which leads me to think that it is a Layer 7 (i.e. Nextcloud) issue. What’s going on here? How can Nextcloud even tell that it’s been placed on a bridged network?\n
\n
**EDIT (2024-01-16T00:19Z):**\n
\n
I performed a network capture on the device running Nextcloud, and it appears that it’s receiving the incoming request (`SYN`), and responds appropriately (`SYN, ACK`), but then Router B responds with `Destination unreachable (Network unreachable)`, which is then, of course, followed by many requests for retransmission as the packets are being dropped. But what’s causing the packets to be dropped? Why aren’t they making it through the network?\n
\n
**EDIT (2024-01-25T08:37Z):**\n
\n
I’m not 100% sure what the previous problem was, but I think that it had to do with [the bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that I was using – not necessarily that it was broken, but perhaps it was jsut incompatible with the setup in some way. What I ended up doing was buying [a different router that supported WDS](https://web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/E8450-CA.html), and then I created a WDS bridge between the two routers. The network seems to be working reliably, and as expected now.
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 4
+favouriteCount: 21
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1728530527 {#2364
date: 2024-10-10 05:22:07.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1909 …}
+votes: Doctrine\ORM\PersistentCollection {#1410 …}
+reports: Doctrine\ORM\PersistentCollection {#1907 …}
+favourites: Doctrine\ORM\PersistentCollection {#1407 …}
+notifications: Doctrine\ORM\PersistentCollection {#2391 …}
+badges: Doctrine\ORM\PersistentCollection {#2369 …}
+children: [
App\Entity\EntryComment {#1611
+user: App\Entity\User {#260 …}
+entry: Proxies\__CG__\App\Entity\Entry {#2452 …2}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+parent: Proxies\__CG__\App\Entity\EntryComment {#1722 …}
+root: Proxies\__CG__\App\Entity\EntryComment {#1721 …}
+body: "I’m not exactly sure what the previous issue was, but it appears that, possibly, [the previous bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that was in use was broken in some way. I have since switched the primary router to one that supports WDS, and created a WDS bridge between the two, and now everything is working as expected."
+lang: "en"
+isAdult: false
+favouriteCount: 1
+score: 0
+lastActive: DateTime @1706171781 {#1596
date: 2024-01-25 09:36:21.0 +01:00
}
+ip: null
+tags: null
+mentions: [
"@Kalcifer@sh.itjust.works"
"@deadbeef@lemmy.nz"
"@vegetaaaaaaa@lemmy.world"
]
+children: Doctrine\ORM\PersistentCollection {#1728 …}
+nested: Doctrine\ORM\PersistentCollection {#1730 …}
+votes: Doctrine\ORM\PersistentCollection {#1734 …}
+reports: Doctrine\ORM\PersistentCollection {#1727 …}
+favourites: Doctrine\ORM\PersistentCollection {#2457 …}
+notifications: Doctrine\ORM\PersistentCollection {#1617 …}
-id: 338798
-bodyTs: "'/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':21 'appear':13 'bridg':18,47 'broken':27 'creat':44 'everyth':53 'exact':4 'expect':57 'issu':9 'm':2 'one':39 'possibl':15 'previous':8,17 'primari':36 'router':37 'sinc':33 'support':41 'sure':5 'switch':34 'two':50 'use':25 'way':30 'wds':42,46 'web.archive.org':20 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':19 'work':55"
+ranking: 0
+commentCount: 0
+upVotes: 0
+downVotes: 0
+visibility: "visible "
+apId: "https://sh.itjust.works/comment/8020902"
+editedAt: null
+createdAt: DateTimeImmutable @1706171781 {#1555
date: 2024-01-25 09:36:21.0 +01:00
}
+"title": 338798
}
]
-id: 30810
-titleTs: "'bridg':12 'move':9 'network':13 'nextcloud':2 'portforward':3 'stop':4 'work':5 'workaround':1"
-bodyTs: "'-01':149,226 '-16':150 '-25':227 '/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':15 '/post/12856689](https://sh.itjust.works/post/12856689)':7 '/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':253 '/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':291 '100':233 '19z':152 '2':82 '2024':148,225 '37z':229 '7':124 'ack':178 'ad':32 'anymor':77 'appear':165 'appropri':176 'aren':216 'b':36,56,182 'bridg':34,45,78,145,250,298 'broken':263 'buy':282 'cannot':69 'captur':157 'caus':209 'connect':24,70 'cours':193 'creat':295 'cross':2 'cross-post':1 'destin':185 'devic':17,42,160 'differ':88,284 'doesn':111 'drop':205,214 'edit':147,224 'end':278 'even':136 'expect':312 'fact':95 'fine':104 'follow':11,194 'go':130 'howev':47 'i.e':125 'incom':171 'incompat':269 'ip':76 'issu':127 'jsut':268 'layer':81,123 'lead':115 'like':99 'm':231 'make':86,219 'mani':196 'move':39,53 'necessarili':259 'network':46,146,156,187,223,304 'nexcloud':72 'nextcloud':19,40,51,109,126,135,162 'oper':79 'packet':202,211 'perfect':103 'perform':154 'perhap':265 'place':142 'portforward':58,105 'post':3 'previous':237 'problem':238 'public':75 'receiv':169 'recent':31 'reflect':92 'reliabl':309 'request':172,197 'respond':175,183 'retransmiss':199 'router':26,35,55,60,181,285,302 'run':18,161 'seem':62,305 'servic':98 'setup':272 'sh.itjust.works':6,14 'sh.itjust.works/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':13 'sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)':5 'snap':20 'soon':49 'ssh':100 'still':101 'stop':64 'support':287 'sure':234 'syn':173,177 't00':151 't08':228 'tell':137 'think':118,242 'topolog':12 'two':301 'unreach':186,188 'use':21,257 'way':275 'wds':288,297 'web.archive.org':252,290 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':251 'web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':289 'whatsoev':89 'work':65,102,113,308"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1705428256
+visibility: "visible "
+apId: "https://sh.itjust.works/post/12856684"
+editedAt: DateTimeImmutable @1728530963 {#2471
date: 2024-10-10 05:29:23.0 +02:00
}
+createdAt: DateTimeImmutable @1705362256 {#2361
date: 2024-01-16 00:44:16.0 +01:00
}
+__isInitialized__: true
…2
} |
|
Show voter details
|
| 4 |
DENIED
|
moderate
|
Proxies\__CG__\App\Entity\Entry {#2452
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "WORKAROUND-Nextcloud-portforward-stops-working-when-it-is-moved-to"
+title: "[WORKAROUND] Nextcloud portforward stops working when it is moved to a bridged network"
+url: null
+body: """
cross-posted to: [sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)\n
\n
---\n
\n
I have the following topology:\n
\n
\n
\n
The device running Nextcloud (snap) used to be connected to Router A, but I have recently added a bridge (Router B) and I moved Nextcloud’s device to that bridged network; however, as soon as Nextcloud was moved to Router B, the portforward on Router A seemed to stop working – as in I cannot connect to nexcloud from the public IP anymore. Bridges operate at layer 2, so this *should* make no difference whatsoever (this is reflected in the fact that other services (like SSH) still work perfectly fine portforwarded – it’s only Nextcloud that doesn’t work), which leads me to think that it is a Layer 7 (i.e. Nextcloud) issue. What’s going on here? How can Nextcloud even tell that it’s been placed on a bridged network?\n
\n
**EDIT (2024-01-16T00:19Z):**\n
\n
I performed a network capture on the device running Nextcloud, and it appears that it’s receiving the incoming request (`SYN`), and responds appropriately (`SYN, ACK`), but then Router B responds with `Destination unreachable (Network unreachable)`, which is then, of course, followed by many requests for retransmission as the packets are being dropped. But what’s causing the packets to be dropped? Why aren’t they making it through the network?\n
\n
**EDIT (2024-01-25T08:37Z):**\n
\n
I’m not 100% sure what the previous problem was, but I think that it had to do with [the bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that I was using – not necessarily that it was broken, but perhaps it was jsut incompatible with the setup in some way. What I ended up doing was buying [a different router that supported WDS](https://web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/E8450-CA.html), and then I created a WDS bridge between the two routers. The network seems to be working reliably, and as expected now.
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 4
+favouriteCount: 21
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1728530527 {#2364
date: 2024-10-10 05:22:07.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1909 …}
+votes: Doctrine\ORM\PersistentCollection {#1410 …}
+reports: Doctrine\ORM\PersistentCollection {#1907 …}
+favourites: Doctrine\ORM\PersistentCollection {#1407 …}
+notifications: Doctrine\ORM\PersistentCollection {#2391 …}
+badges: Doctrine\ORM\PersistentCollection {#2369 …}
+children: [
App\Entity\EntryComment {#1611
+user: App\Entity\User {#260 …}
+entry: Proxies\__CG__\App\Entity\Entry {#2452 …2}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+parent: Proxies\__CG__\App\Entity\EntryComment {#1722 …}
+root: Proxies\__CG__\App\Entity\EntryComment {#1721 …}
+body: "I’m not exactly sure what the previous issue was, but it appears that, possibly, [the previous bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that was in use was broken in some way. I have since switched the primary router to one that supports WDS, and created a WDS bridge between the two, and now everything is working as expected."
+lang: "en"
+isAdult: false
+favouriteCount: 1
+score: 0
+lastActive: DateTime @1706171781 {#1596
date: 2024-01-25 09:36:21.0 +01:00
}
+ip: null
+tags: null
+mentions: [
"@Kalcifer@sh.itjust.works"
"@deadbeef@lemmy.nz"
"@vegetaaaaaaa@lemmy.world"
]
+children: Doctrine\ORM\PersistentCollection {#1728 …}
+nested: Doctrine\ORM\PersistentCollection {#1730 …}
+votes: Doctrine\ORM\PersistentCollection {#1734 …}
+reports: Doctrine\ORM\PersistentCollection {#1727 …}
+favourites: Doctrine\ORM\PersistentCollection {#2457 …}
+notifications: Doctrine\ORM\PersistentCollection {#1617 …}
-id: 338798
-bodyTs: "'/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':21 'appear':13 'bridg':18,47 'broken':27 'creat':44 'everyth':53 'exact':4 'expect':57 'issu':9 'm':2 'one':39 'possibl':15 'previous':8,17 'primari':36 'router':37 'sinc':33 'support':41 'sure':5 'switch':34 'two':50 'use':25 'way':30 'wds':42,46 'web.archive.org':20 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':19 'work':55"
+ranking: 0
+commentCount: 0
+upVotes: 0
+downVotes: 0
+visibility: "visible "
+apId: "https://sh.itjust.works/comment/8020902"
+editedAt: null
+createdAt: DateTimeImmutable @1706171781 {#1555
date: 2024-01-25 09:36:21.0 +01:00
}
+"title": 338798
}
]
-id: 30810
-titleTs: "'bridg':12 'move':9 'network':13 'nextcloud':2 'portforward':3 'stop':4 'work':5 'workaround':1"
-bodyTs: "'-01':149,226 '-16':150 '-25':227 '/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':15 '/post/12856689](https://sh.itjust.works/post/12856689)':7 '/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':253 '/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':291 '100':233 '19z':152 '2':82 '2024':148,225 '37z':229 '7':124 'ack':178 'ad':32 'anymor':77 'appear':165 'appropri':176 'aren':216 'b':36,56,182 'bridg':34,45,78,145,250,298 'broken':263 'buy':282 'cannot':69 'captur':157 'caus':209 'connect':24,70 'cours':193 'creat':295 'cross':2 'cross-post':1 'destin':185 'devic':17,42,160 'differ':88,284 'doesn':111 'drop':205,214 'edit':147,224 'end':278 'even':136 'expect':312 'fact':95 'fine':104 'follow':11,194 'go':130 'howev':47 'i.e':125 'incom':171 'incompat':269 'ip':76 'issu':127 'jsut':268 'layer':81,123 'lead':115 'like':99 'm':231 'make':86,219 'mani':196 'move':39,53 'necessarili':259 'network':46,146,156,187,223,304 'nexcloud':72 'nextcloud':19,40,51,109,126,135,162 'oper':79 'packet':202,211 'perfect':103 'perform':154 'perhap':265 'place':142 'portforward':58,105 'post':3 'previous':237 'problem':238 'public':75 'receiv':169 'recent':31 'reflect':92 'reliabl':309 'request':172,197 'respond':175,183 'retransmiss':199 'router':26,35,55,60,181,285,302 'run':18,161 'seem':62,305 'servic':98 'setup':272 'sh.itjust.works':6,14 'sh.itjust.works/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':13 'sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)':5 'snap':20 'soon':49 'ssh':100 'still':101 'stop':64 'support':287 'sure':234 'syn':173,177 't00':151 't08':228 'tell':137 'think':118,242 'topolog':12 'two':301 'unreach':186,188 'use':21,257 'way':275 'wds':288,297 'web.archive.org':252,290 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':251 'web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':289 'whatsoev':89 'work':65,102,113,308"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1705428256
+visibility: "visible "
+apId: "https://sh.itjust.works/post/12856684"
+editedAt: DateTimeImmutable @1728530963 {#2471
date: 2024-10-10 05:29:23.0 +02:00
}
+createdAt: DateTimeImmutable @1705362256 {#2361
date: 2024-01-16 00:44:16.0 +01:00
}
+__isInitialized__: true
…2
} |
|
Show voter details
|
| 5 |
DENIED
|
ROLE_USER
|
null |
|
Show voter details
|
| 6 |
DENIED
|
moderate
|
App\Entity\EntryComment {#1611
+user: App\Entity\User {#260 …}
+entry: Proxies\__CG__\App\Entity\Entry {#2452
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "WORKAROUND-Nextcloud-portforward-stops-working-when-it-is-moved-to"
+title: "[WORKAROUND] Nextcloud portforward stops working when it is moved to a bridged network"
+url: null
+body: """
cross-posted to: [sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)\n
\n
---\n
\n
I have the following topology:\n
\n
\n
\n
The device running Nextcloud (snap) used to be connected to Router A, but I have recently added a bridge (Router B) and I moved Nextcloud’s device to that bridged network; however, as soon as Nextcloud was moved to Router B, the portforward on Router A seemed to stop working – as in I cannot connect to nexcloud from the public IP anymore. Bridges operate at layer 2, so this *should* make no difference whatsoever (this is reflected in the fact that other services (like SSH) still work perfectly fine portforwarded – it’s only Nextcloud that doesn’t work), which leads me to think that it is a Layer 7 (i.e. Nextcloud) issue. What’s going on here? How can Nextcloud even tell that it’s been placed on a bridged network?\n
\n
**EDIT (2024-01-16T00:19Z):**\n
\n
I performed a network capture on the device running Nextcloud, and it appears that it’s receiving the incoming request (`SYN`), and responds appropriately (`SYN, ACK`), but then Router B responds with `Destination unreachable (Network unreachable)`, which is then, of course, followed by many requests for retransmission as the packets are being dropped. But what’s causing the packets to be dropped? Why aren’t they making it through the network?\n
\n
**EDIT (2024-01-25T08:37Z):**\n
\n
I’m not 100% sure what the previous problem was, but I think that it had to do with [the bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that I was using – not necessarily that it was broken, but perhaps it was jsut incompatible with the setup in some way. What I ended up doing was buying [a different router that supported WDS](https://web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/E8450-CA.html), and then I created a WDS bridge between the two routers. The network seems to be working reliably, and as expected now.
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 4
+favouriteCount: 21
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1728530527 {#2364
date: 2024-10-10 05:22:07.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1909 …}
+votes: Doctrine\ORM\PersistentCollection {#1410 …}
+reports: Doctrine\ORM\PersistentCollection {#1907 …}
+favourites: Doctrine\ORM\PersistentCollection {#1407 …}
+notifications: Doctrine\ORM\PersistentCollection {#2391 …}
+badges: Doctrine\ORM\PersistentCollection {#2369 …}
+children: [
App\Entity\EntryComment {#1611}
]
-id: 30810
-titleTs: "'bridg':12 'move':9 'network':13 'nextcloud':2 'portforward':3 'stop':4 'work':5 'workaround':1"
-bodyTs: "'-01':149,226 '-16':150 '-25':227 '/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':15 '/post/12856689](https://sh.itjust.works/post/12856689)':7 '/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':253 '/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':291 '100':233 '19z':152 '2':82 '2024':148,225 '37z':229 '7':124 'ack':178 'ad':32 'anymor':77 'appear':165 'appropri':176 'aren':216 'b':36,56,182 'bridg':34,45,78,145,250,298 'broken':263 'buy':282 'cannot':69 'captur':157 'caus':209 'connect':24,70 'cours':193 'creat':295 'cross':2 'cross-post':1 'destin':185 'devic':17,42,160 'differ':88,284 'doesn':111 'drop':205,214 'edit':147,224 'end':278 'even':136 'expect':312 'fact':95 'fine':104 'follow':11,194 'go':130 'howev':47 'i.e':125 'incom':171 'incompat':269 'ip':76 'issu':127 'jsut':268 'layer':81,123 'lead':115 'like':99 'm':231 'make':86,219 'mani':196 'move':39,53 'necessarili':259 'network':46,146,156,187,223,304 'nexcloud':72 'nextcloud':19,40,51,109,126,135,162 'oper':79 'packet':202,211 'perfect':103 'perform':154 'perhap':265 'place':142 'portforward':58,105 'post':3 'previous':237 'problem':238 'public':75 'receiv':169 'recent':31 'reflect':92 'reliabl':309 'request':172,197 'respond':175,183 'retransmiss':199 'router':26,35,55,60,181,285,302 'run':18,161 'seem':62,305 'servic':98 'setup':272 'sh.itjust.works':6,14 'sh.itjust.works/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':13 'sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)':5 'snap':20 'soon':49 'ssh':100 'still':101 'stop':64 'support':287 'sure':234 'syn':173,177 't00':151 't08':228 'tell':137 'think':118,242 'topolog':12 'two':301 'unreach':186,188 'use':21,257 'way':275 'wds':288,297 'web.archive.org':252,290 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':251 'web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':289 'whatsoev':89 'work':65,102,113,308"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1705428256
+visibility: "visible "
+apId: "https://sh.itjust.works/post/12856684"
+editedAt: DateTimeImmutable @1728530963 {#2471
date: 2024-10-10 05:29:23.0 +02:00
}
+createdAt: DateTimeImmutable @1705362256 {#2361
date: 2024-01-16 00:44:16.0 +01:00
}
+__isInitialized__: true
…2
}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+parent: Proxies\__CG__\App\Entity\EntryComment {#1722 …}
+root: Proxies\__CG__\App\Entity\EntryComment {#1721 …}
+body: "I’m not exactly sure what the previous issue was, but it appears that, possibly, [the previous bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that was in use was broken in some way. I have since switched the primary router to one that supports WDS, and created a WDS bridge between the two, and now everything is working as expected."
+lang: "en"
+isAdult: false
+favouriteCount: 1
+score: 0
+lastActive: DateTime @1706171781 {#1596
date: 2024-01-25 09:36:21.0 +01:00
}
+ip: null
+tags: null
+mentions: [
"@Kalcifer@sh.itjust.works"
"@deadbeef@lemmy.nz"
"@vegetaaaaaaa@lemmy.world"
]
+children: Doctrine\ORM\PersistentCollection {#1728 …}
+nested: Doctrine\ORM\PersistentCollection {#1730 …}
+votes: Doctrine\ORM\PersistentCollection {#1734 …}
+reports: Doctrine\ORM\PersistentCollection {#1727 …}
+favourites: Doctrine\ORM\PersistentCollection {#2457 …}
+notifications: Doctrine\ORM\PersistentCollection {#1617 …}
-id: 338798
-bodyTs: "'/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':21 'appear':13 'bridg':18,47 'broken':27 'creat':44 'everyth':53 'exact':4 'expect':57 'issu':9 'm':2 'one':39 'possibl':15 'previous':8,17 'primari':36 'router':37 'sinc':33 'support':41 'sure':5 'switch':34 'two':50 'use':25 'way':30 'wds':42,46 'web.archive.org':20 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':19 'work':55"
+ranking: 0
+commentCount: 0
+upVotes: 0
+downVotes: 0
+visibility: "visible "
+apId: "https://sh.itjust.works/comment/8020902"
+editedAt: null
+createdAt: DateTimeImmutable @1706171781 {#1555
date: 2024-01-25 09:36:21.0 +01:00
}
+"title": 338798
} |
|
Show voter details
|
| 7 |
DENIED
|
edit
|
App\Entity\EntryComment {#1611
+user: App\Entity\User {#260 …}
+entry: Proxies\__CG__\App\Entity\Entry {#2452
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "WORKAROUND-Nextcloud-portforward-stops-working-when-it-is-moved-to"
+title: "[WORKAROUND] Nextcloud portforward stops working when it is moved to a bridged network"
+url: null
+body: """
cross-posted to: [sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)\n
\n
---\n
\n
I have the following topology:\n
\n
\n
\n
The device running Nextcloud (snap) used to be connected to Router A, but I have recently added a bridge (Router B) and I moved Nextcloud’s device to that bridged network; however, as soon as Nextcloud was moved to Router B, the portforward on Router A seemed to stop working – as in I cannot connect to nexcloud from the public IP anymore. Bridges operate at layer 2, so this *should* make no difference whatsoever (this is reflected in the fact that other services (like SSH) still work perfectly fine portforwarded – it’s only Nextcloud that doesn’t work), which leads me to think that it is a Layer 7 (i.e. Nextcloud) issue. What’s going on here? How can Nextcloud even tell that it’s been placed on a bridged network?\n
\n
**EDIT (2024-01-16T00:19Z):**\n
\n
I performed a network capture on the device running Nextcloud, and it appears that it’s receiving the incoming request (`SYN`), and responds appropriately (`SYN, ACK`), but then Router B responds with `Destination unreachable (Network unreachable)`, which is then, of course, followed by many requests for retransmission as the packets are being dropped. But what’s causing the packets to be dropped? Why aren’t they making it through the network?\n
\n
**EDIT (2024-01-25T08:37Z):**\n
\n
I’m not 100% sure what the previous problem was, but I think that it had to do with [the bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that I was using – not necessarily that it was broken, but perhaps it was jsut incompatible with the setup in some way. What I ended up doing was buying [a different router that supported WDS](https://web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/E8450-CA.html), and then I created a WDS bridge between the two routers. The network seems to be working reliably, and as expected now.
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 4
+favouriteCount: 21
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1728530527 {#2364
date: 2024-10-10 05:22:07.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1909 …}
+votes: Doctrine\ORM\PersistentCollection {#1410 …}
+reports: Doctrine\ORM\PersistentCollection {#1907 …}
+favourites: Doctrine\ORM\PersistentCollection {#1407 …}
+notifications: Doctrine\ORM\PersistentCollection {#2391 …}
+badges: Doctrine\ORM\PersistentCollection {#2369 …}
+children: [
App\Entity\EntryComment {#1611}
]
-id: 30810
-titleTs: "'bridg':12 'move':9 'network':13 'nextcloud':2 'portforward':3 'stop':4 'work':5 'workaround':1"
-bodyTs: "'-01':149,226 '-16':150 '-25':227 '/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':15 '/post/12856689](https://sh.itjust.works/post/12856689)':7 '/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':253 '/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':291 '100':233 '19z':152 '2':82 '2024':148,225 '37z':229 '7':124 'ack':178 'ad':32 'anymor':77 'appear':165 'appropri':176 'aren':216 'b':36,56,182 'bridg':34,45,78,145,250,298 'broken':263 'buy':282 'cannot':69 'captur':157 'caus':209 'connect':24,70 'cours':193 'creat':295 'cross':2 'cross-post':1 'destin':185 'devic':17,42,160 'differ':88,284 'doesn':111 'drop':205,214 'edit':147,224 'end':278 'even':136 'expect':312 'fact':95 'fine':104 'follow':11,194 'go':130 'howev':47 'i.e':125 'incom':171 'incompat':269 'ip':76 'issu':127 'jsut':268 'layer':81,123 'lead':115 'like':99 'm':231 'make':86,219 'mani':196 'move':39,53 'necessarili':259 'network':46,146,156,187,223,304 'nexcloud':72 'nextcloud':19,40,51,109,126,135,162 'oper':79 'packet':202,211 'perfect':103 'perform':154 'perhap':265 'place':142 'portforward':58,105 'post':3 'previous':237 'problem':238 'public':75 'receiv':169 'recent':31 'reflect':92 'reliabl':309 'request':172,197 'respond':175,183 'retransmiss':199 'router':26,35,55,60,181,285,302 'run':18,161 'seem':62,305 'servic':98 'setup':272 'sh.itjust.works':6,14 'sh.itjust.works/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':13 'sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)':5 'snap':20 'soon':49 'ssh':100 'still':101 'stop':64 'support':287 'sure':234 'syn':173,177 't00':151 't08':228 'tell':137 'think':118,242 'topolog':12 'two':301 'unreach':186,188 'use':21,257 'way':275 'wds':288,297 'web.archive.org':252,290 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':251 'web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':289 'whatsoev':89 'work':65,102,113,308"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1705428256
+visibility: "visible "
+apId: "https://sh.itjust.works/post/12856684"
+editedAt: DateTimeImmutable @1728530963 {#2471
date: 2024-10-10 05:29:23.0 +02:00
}
+createdAt: DateTimeImmutable @1705362256 {#2361
date: 2024-01-16 00:44:16.0 +01:00
}
+__isInitialized__: true
…2
}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+parent: Proxies\__CG__\App\Entity\EntryComment {#1722 …}
+root: Proxies\__CG__\App\Entity\EntryComment {#1721 …}
+body: "I’m not exactly sure what the previous issue was, but it appears that, possibly, [the previous bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that was in use was broken in some way. I have since switched the primary router to one that supports WDS, and created a WDS bridge between the two, and now everything is working as expected."
+lang: "en"
+isAdult: false
+favouriteCount: 1
+score: 0
+lastActive: DateTime @1706171781 {#1596
date: 2024-01-25 09:36:21.0 +01:00
}
+ip: null
+tags: null
+mentions: [
"@Kalcifer@sh.itjust.works"
"@deadbeef@lemmy.nz"
"@vegetaaaaaaa@lemmy.world"
]
+children: Doctrine\ORM\PersistentCollection {#1728 …}
+nested: Doctrine\ORM\PersistentCollection {#1730 …}
+votes: Doctrine\ORM\PersistentCollection {#1734 …}
+reports: Doctrine\ORM\PersistentCollection {#1727 …}
+favourites: Doctrine\ORM\PersistentCollection {#2457 …}
+notifications: Doctrine\ORM\PersistentCollection {#1617 …}
-id: 338798
-bodyTs: "'/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':21 'appear':13 'bridg':18,47 'broken':27 'creat':44 'everyth':53 'exact':4 'expect':57 'issu':9 'm':2 'one':39 'possibl':15 'previous':8,17 'primari':36 'router':37 'sinc':33 'support':41 'sure':5 'switch':34 'two':50 'use':25 'way':30 'wds':42,46 'web.archive.org':20 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':19 'work':55"
+ranking: 0
+commentCount: 0
+upVotes: 0
+downVotes: 0
+visibility: "visible "
+apId: "https://sh.itjust.works/comment/8020902"
+editedAt: null
+createdAt: DateTimeImmutable @1706171781 {#1555
date: 2024-01-25 09:36:21.0 +01:00
}
+"title": 338798
} |
|
Show voter details
|
| 8 |
DENIED
|
moderate
|
App\Entity\EntryComment {#1611
+user: App\Entity\User {#260 …}
+entry: Proxies\__CG__\App\Entity\Entry {#2452
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "WORKAROUND-Nextcloud-portforward-stops-working-when-it-is-moved-to"
+title: "[WORKAROUND] Nextcloud portforward stops working when it is moved to a bridged network"
+url: null
+body: """
cross-posted to: [sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)\n
\n
---\n
\n
I have the following topology:\n
\n
\n
\n
The device running Nextcloud (snap) used to be connected to Router A, but I have recently added a bridge (Router B) and I moved Nextcloud’s device to that bridged network; however, as soon as Nextcloud was moved to Router B, the portforward on Router A seemed to stop working – as in I cannot connect to nexcloud from the public IP anymore. Bridges operate at layer 2, so this *should* make no difference whatsoever (this is reflected in the fact that other services (like SSH) still work perfectly fine portforwarded – it’s only Nextcloud that doesn’t work), which leads me to think that it is a Layer 7 (i.e. Nextcloud) issue. What’s going on here? How can Nextcloud even tell that it’s been placed on a bridged network?\n
\n
**EDIT (2024-01-16T00:19Z):**\n
\n
I performed a network capture on the device running Nextcloud, and it appears that it’s receiving the incoming request (`SYN`), and responds appropriately (`SYN, ACK`), but then Router B responds with `Destination unreachable (Network unreachable)`, which is then, of course, followed by many requests for retransmission as the packets are being dropped. But what’s causing the packets to be dropped? Why aren’t they making it through the network?\n
\n
**EDIT (2024-01-25T08:37Z):**\n
\n
I’m not 100% sure what the previous problem was, but I think that it had to do with [the bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that I was using – not necessarily that it was broken, but perhaps it was jsut incompatible with the setup in some way. What I ended up doing was buying [a different router that supported WDS](https://web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/E8450-CA.html), and then I created a WDS bridge between the two routers. The network seems to be working reliably, and as expected now.
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 4
+favouriteCount: 21
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1728530527 {#2364
date: 2024-10-10 05:22:07.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1909 …}
+votes: Doctrine\ORM\PersistentCollection {#1410 …}
+reports: Doctrine\ORM\PersistentCollection {#1907 …}
+favourites: Doctrine\ORM\PersistentCollection {#1407 …}
+notifications: Doctrine\ORM\PersistentCollection {#2391 …}
+badges: Doctrine\ORM\PersistentCollection {#2369 …}
+children: [
App\Entity\EntryComment {#1611}
]
-id: 30810
-titleTs: "'bridg':12 'move':9 'network':13 'nextcloud':2 'portforward':3 'stop':4 'work':5 'workaround':1"
-bodyTs: "'-01':149,226 '-16':150 '-25':227 '/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':15 '/post/12856689](https://sh.itjust.works/post/12856689)':7 '/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':253 '/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':291 '100':233 '19z':152 '2':82 '2024':148,225 '37z':229 '7':124 'ack':178 'ad':32 'anymor':77 'appear':165 'appropri':176 'aren':216 'b':36,56,182 'bridg':34,45,78,145,250,298 'broken':263 'buy':282 'cannot':69 'captur':157 'caus':209 'connect':24,70 'cours':193 'creat':295 'cross':2 'cross-post':1 'destin':185 'devic':17,42,160 'differ':88,284 'doesn':111 'drop':205,214 'edit':147,224 'end':278 'even':136 'expect':312 'fact':95 'fine':104 'follow':11,194 'go':130 'howev':47 'i.e':125 'incom':171 'incompat':269 'ip':76 'issu':127 'jsut':268 'layer':81,123 'lead':115 'like':99 'm':231 'make':86,219 'mani':196 'move':39,53 'necessarili':259 'network':46,146,156,187,223,304 'nexcloud':72 'nextcloud':19,40,51,109,126,135,162 'oper':79 'packet':202,211 'perfect':103 'perform':154 'perhap':265 'place':142 'portforward':58,105 'post':3 'previous':237 'problem':238 'public':75 'receiv':169 'recent':31 'reflect':92 'reliabl':309 'request':172,197 'respond':175,183 'retransmiss':199 'router':26,35,55,60,181,285,302 'run':18,161 'seem':62,305 'servic':98 'setup':272 'sh.itjust.works':6,14 'sh.itjust.works/pictrs/image/f134ad1b-a822-45ed-a9a8-387fdecafac6.png)':13 'sh.itjust.works/post/12856689](https://sh.itjust.works/post/12856689)':5 'snap':20 'soon':49 'ssh':100 'still':101 'stop':64 'support':287 'sure':234 'syn':173,177 't00':151 't08':228 'tell':137 'think':118,242 'topolog':12 'two':301 'unreach':186,188 'use':21,257 'way':275 'wds':288,297 'web.archive.org':252,290 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':251 'web.archive.org/web/20240120035823/https://www.linksys.com/ca/dual-band-ax3200-wifi-6-router-e8450/e8450-ca.html),':289 'whatsoev':89 'work':65,102,113,308"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1705428256
+visibility: "visible "
+apId: "https://sh.itjust.works/post/12856684"
+editedAt: DateTimeImmutable @1728530963 {#2471
date: 2024-10-10 05:29:23.0 +02:00
}
+createdAt: DateTimeImmutable @1705362256 {#2361
date: 2024-01-16 00:44:16.0 +01:00
}
+__isInitialized__: true
…2
}
+magazine: Proxies\__CG__\App\Entity\Magazine {#2453 …}
+image: null
+parent: Proxies\__CG__\App\Entity\EntryComment {#1722 …}
+root: Proxies\__CG__\App\Entity\EntryComment {#1721 …}
+body: "I’m not exactly sure what the previous issue was, but it appears that, possibly, [the previous bridge](https://web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration) that was in use was broken in some way. I have since switched the primary router to one that supports WDS, and created a WDS bridge between the two, and now everything is working as expected."
+lang: "en"
+isAdult: false
+favouriteCount: 1
+score: 0
+lastActive: DateTime @1706171781 {#1596
date: 2024-01-25 09:36:21.0 +01:00
}
+ip: null
+tags: null
+mentions: [
"@Kalcifer@sh.itjust.works"
"@deadbeef@lemmy.nz"
"@vegetaaaaaaa@lemmy.world"
]
+children: Doctrine\ORM\PersistentCollection {#1728 …}
+nested: Doctrine\ORM\PersistentCollection {#1730 …}
+votes: Doctrine\ORM\PersistentCollection {#1734 …}
+reports: Doctrine\ORM\PersistentCollection {#1727 …}
+favourites: Doctrine\ORM\PersistentCollection {#2457 …}
+notifications: Doctrine\ORM\PersistentCollection {#1617 …}
-id: 338798
-bodyTs: "'/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':21 'appear':13 'bridg':18,47 'broken':27 'creat':44 'everyth':53 'exact':4 'expect':57 'issu':9 'm':2 'one':39 'possibl':15 'previous':8,17 'primari':36 'router':37 'sinc':33 'support':41 'sure':5 'switch':34 'two':50 'use':25 'way':30 'wds':42,46 'web.archive.org':20 'web.archive.org/web/2/https://openwrt.org/docs/guide-user/network/wifi/relay_configuration)':19 'work':55"
+ranking: 0
+commentCount: 0
+upVotes: 0
+downVotes: 0
+visibility: "visible "
+apId: "https://sh.itjust.works/comment/8020902"
+editedAt: null
+createdAt: DateTimeImmutable @1706171781 {#1555
date: 2024-01-25 09:36:21.0 +01:00
}
+"title": 338798
} |
|
Show voter details
|
| 9 |
DENIED
|
ROLE_USER
|
null |
|
Show voter details
|
| 10 |
DENIED
|
moderate
|
App\Entity\Entry {#1700
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#1581 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "When-do-I-actually-need-a-firewall"
+title: "When do I actually need a firewall?"
+url: null
+body: """
I’ve spent some time searching this question, but I have yet to find a satisfying answer. The majority of answers that I have seen state something along the lines of the following:\n
\n
1. “It’s just good security practice.”\n
2. “You need it if you are running a server.”\n
3. “You need it if you don’t trust the other devices on the network.”\n
4. “You need it if you are not behind a NAT.”\n
5. “You need it if you don’t trust the software running on your computer.”\n
\n
The only answer that makes any sense to me is #5. #1 leaves a lot to be desired, as it advocates for doing something without thinking about why you’re doing it – it is essentially a non-answer. #2 is strange – why does it matter? If one is hosting a webserver on port 80, for example, they are going to poke a hole in their router’s NAT at port 80 to open that server’s port to the public. What difference does it make to then have another firewall that needs to be port forwarded? #3 is a strange one – what sort of malicious behaviour could even be done to a device with no firewall? If you have no applications listening on any port, then there’s nothing to access. #4 feels like an extension of #3 – only, in this case, it is most likely a larger group that the device is exposed to. #5 is the only one that makes some sense; if you install a program that you do not trust (you don’t know how it works), you don’t want it to be able to readily communicate with the outside world unless you explicitly grant it permission to do so. Such an unknown program could be the door to get into your device, or a spy on your device’s actions.\n
\n
If anything, a firewall only seems to provide extra precautions against mistakes made by the user, rather than actively preventing bad actors from getting in. People seem to treat it as if it’s acting like the front door to a house, but this analogy doesn’t make much sense to me – without a house (a service listening on a port), what good is a door?
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 40
+favouriteCount: 91
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1729354440 {#1421
date: 2024-10-19 18:14:00.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1652 …}
+votes: Doctrine\ORM\PersistentCollection {#1649 …}
+reports: Doctrine\ORM\PersistentCollection {#1656 …}
+favourites: Doctrine\ORM\PersistentCollection {#1527 …}
+notifications: Doctrine\ORM\PersistentCollection {#1560 …}
+badges: Doctrine\ORM\PersistentCollection {#1558 …}
+children: []
-id: 32961
-titleTs: "'actual':4 'firewal':7 'need':5"
-bodyTs: "'1':34,103 '2':41,131 '3':51,189,230 '4':66,224 '5':77,102,248 '80':146,163 'abl':281 'access':223 'act':353 'action':318 'activ':337 'actor':340 'advoc':112 'along':28 'analog':363 'anoth':181 'answer':17,21,94,130 'anyth':320 'applic':213 'bad':339 'behaviour':198 'behind':74 'case':234 'communic':284 'comput':91 'could':199,302 'desir':109 'devic':62,205,244,310,316 'differ':174 'doesn':364 'done':202 'door':305,357,384 'essenti':126 'even':200 'exampl':148 'explicit':291 'expos':246 'extens':228 'extra':327 'feel':225 'find':14 'firewal':182,208,322 'follow':33 'forward':188 'front':356 'get':307,342 'go':151 'good':38,381 'grant':292 'group':241 'hole':155 'host':141 'hous':360,373 'instal':259 'know':270 'larger':240 'leav':104 'like':226,238,354 'line':30 'listen':214,376 'lot':106 'made':331 'major':19 'make':96,177,254,366 'malici':197 'matter':137 'mistak':330 'much':367 'nat':76,160 'need':43,53,68,79,184 'network':65 'non':129 'non-answ':128 'noth':221 'one':139,193,252 'open':165 'outsid':287 'peopl':344 'permiss':294 'poke':153 'port':145,162,169,187,217,379 'practic':40 'precaut':328 'prevent':338 'program':261,301 'provid':326 'public':172 'question':8 'rather':335 're':121 'readili':283 'router':158 'run':48,88 'satisfi':16 'search':6 'secur':39 'seem':324,345 'seen':25 'sens':98,256,368 'server':50,167 'servic':375 'softwar':87 'someth':27,115 'sort':195 'spent':3 'spi':313 'state':26 'strang':133,192 'think':117 'time':5 'treat':347 'trust':59,85,266 'unknown':300 'unless':289 'user':334 've':2 'want':277 'webserv':143 'without':116,371 'work':273 'world':288 'yet':12"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1706257325
+visibility: "visible "
+apId: "https://sh.itjust.works/post/13453975"
+editedAt: DateTimeImmutable @1728528893 {#1424
date: 2024-10-10 04:54:53.0 +02:00
}
+createdAt: DateTimeImmutable @1706170925 {#1415
date: 2024-01-25 09:22:05.0 +01:00
}
} |
|
Show voter details
|
| 11 |
DENIED
|
edit
|
App\Entity\Entry {#1700
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#1581 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "When-do-I-actually-need-a-firewall"
+title: "When do I actually need a firewall?"
+url: null
+body: """
I’ve spent some time searching this question, but I have yet to find a satisfying answer. The majority of answers that I have seen state something along the lines of the following:\n
\n
1. “It’s just good security practice.”\n
2. “You need it if you are running a server.”\n
3. “You need it if you don’t trust the other devices on the network.”\n
4. “You need it if you are not behind a NAT.”\n
5. “You need it if you don’t trust the software running on your computer.”\n
\n
The only answer that makes any sense to me is #5. #1 leaves a lot to be desired, as it advocates for doing something without thinking about why you’re doing it – it is essentially a non-answer. #2 is strange – why does it matter? If one is hosting a webserver on port 80, for example, they are going to poke a hole in their router’s NAT at port 80 to open that server’s port to the public. What difference does it make to then have another firewall that needs to be port forwarded? #3 is a strange one – what sort of malicious behaviour could even be done to a device with no firewall? If you have no applications listening on any port, then there’s nothing to access. #4 feels like an extension of #3 – only, in this case, it is most likely a larger group that the device is exposed to. #5 is the only one that makes some sense; if you install a program that you do not trust (you don’t know how it works), you don’t want it to be able to readily communicate with the outside world unless you explicitly grant it permission to do so. Such an unknown program could be the door to get into your device, or a spy on your device’s actions.\n
\n
If anything, a firewall only seems to provide extra precautions against mistakes made by the user, rather than actively preventing bad actors from getting in. People seem to treat it as if it’s acting like the front door to a house, but this analogy doesn’t make much sense to me – without a house (a service listening on a port), what good is a door?
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 40
+favouriteCount: 91
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1729354440 {#1421
date: 2024-10-19 18:14:00.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1652 …}
+votes: Doctrine\ORM\PersistentCollection {#1649 …}
+reports: Doctrine\ORM\PersistentCollection {#1656 …}
+favourites: Doctrine\ORM\PersistentCollection {#1527 …}
+notifications: Doctrine\ORM\PersistentCollection {#1560 …}
+badges: Doctrine\ORM\PersistentCollection {#1558 …}
+children: []
-id: 32961
-titleTs: "'actual':4 'firewal':7 'need':5"
-bodyTs: "'1':34,103 '2':41,131 '3':51,189,230 '4':66,224 '5':77,102,248 '80':146,163 'abl':281 'access':223 'act':353 'action':318 'activ':337 'actor':340 'advoc':112 'along':28 'analog':363 'anoth':181 'answer':17,21,94,130 'anyth':320 'applic':213 'bad':339 'behaviour':198 'behind':74 'case':234 'communic':284 'comput':91 'could':199,302 'desir':109 'devic':62,205,244,310,316 'differ':174 'doesn':364 'done':202 'door':305,357,384 'essenti':126 'even':200 'exampl':148 'explicit':291 'expos':246 'extens':228 'extra':327 'feel':225 'find':14 'firewal':182,208,322 'follow':33 'forward':188 'front':356 'get':307,342 'go':151 'good':38,381 'grant':292 'group':241 'hole':155 'host':141 'hous':360,373 'instal':259 'know':270 'larger':240 'leav':104 'like':226,238,354 'line':30 'listen':214,376 'lot':106 'made':331 'major':19 'make':96,177,254,366 'malici':197 'matter':137 'mistak':330 'much':367 'nat':76,160 'need':43,53,68,79,184 'network':65 'non':129 'non-answ':128 'noth':221 'one':139,193,252 'open':165 'outsid':287 'peopl':344 'permiss':294 'poke':153 'port':145,162,169,187,217,379 'practic':40 'precaut':328 'prevent':338 'program':261,301 'provid':326 'public':172 'question':8 'rather':335 're':121 'readili':283 'router':158 'run':48,88 'satisfi':16 'search':6 'secur':39 'seem':324,345 'seen':25 'sens':98,256,368 'server':50,167 'servic':375 'softwar':87 'someth':27,115 'sort':195 'spent':3 'spi':313 'state':26 'strang':133,192 'think':117 'time':5 'treat':347 'trust':59,85,266 'unknown':300 'unless':289 'user':334 've':2 'want':277 'webserv':143 'without':116,371 'work':273 'world':288 'yet':12"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1706257325
+visibility: "visible "
+apId: "https://sh.itjust.works/post/13453975"
+editedAt: DateTimeImmutable @1728528893 {#1424
date: 2024-10-10 04:54:53.0 +02:00
}
+createdAt: DateTimeImmutable @1706170925 {#1415
date: 2024-01-25 09:22:05.0 +01:00
}
} |
|
Show voter details
|
| 12 |
DENIED
|
moderate
|
App\Entity\Entry {#1700
+user: App\Entity\User {#260 …}
+magazine: Proxies\__CG__\App\Entity\Magazine {#1581 …}
+image: null
+domain: Proxies\__CG__\App\Entity\Domain {#1654 …}
+slug: "When-do-I-actually-need-a-firewall"
+title: "When do I actually need a firewall?"
+url: null
+body: """
I’ve spent some time searching this question, but I have yet to find a satisfying answer. The majority of answers that I have seen state something along the lines of the following:\n
\n
1. “It’s just good security practice.”\n
2. “You need it if you are running a server.”\n
3. “You need it if you don’t trust the other devices on the network.”\n
4. “You need it if you are not behind a NAT.”\n
5. “You need it if you don’t trust the software running on your computer.”\n
\n
The only answer that makes any sense to me is #5. #1 leaves a lot to be desired, as it advocates for doing something without thinking about why you’re doing it – it is essentially a non-answer. #2 is strange – why does it matter? If one is hosting a webserver on port 80, for example, they are going to poke a hole in their router’s NAT at port 80 to open that server’s port to the public. What difference does it make to then have another firewall that needs to be port forwarded? #3 is a strange one – what sort of malicious behaviour could even be done to a device with no firewall? If you have no applications listening on any port, then there’s nothing to access. #4 feels like an extension of #3 – only, in this case, it is most likely a larger group that the device is exposed to. #5 is the only one that makes some sense; if you install a program that you do not trust (you don’t know how it works), you don’t want it to be able to readily communicate with the outside world unless you explicitly grant it permission to do so. Such an unknown program could be the door to get into your device, or a spy on your device’s actions.\n
\n
If anything, a firewall only seems to provide extra precautions against mistakes made by the user, rather than actively preventing bad actors from getting in. People seem to treat it as if it’s acting like the front door to a house, but this analogy doesn’t make much sense to me – without a house (a service listening on a port), what good is a door?
"""
+type: "article"
+lang: "en"
+isOc: false
+hasEmbed: false
+commentCount: 40
+favouriteCount: 91
+score: 0
+isAdult: false
+sticky: false
+lastActive: DateTime @1729354440 {#1421
date: 2024-10-19 18:14:00.0 +02:00
}
+ip: null
+adaAmount: 0
+tags: null
+mentions: null
+comments: Doctrine\ORM\PersistentCollection {#1652 …}
+votes: Doctrine\ORM\PersistentCollection {#1649 …}
+reports: Doctrine\ORM\PersistentCollection {#1656 …}
+favourites: Doctrine\ORM\PersistentCollection {#1527 …}
+notifications: Doctrine\ORM\PersistentCollection {#1560 …}
+badges: Doctrine\ORM\PersistentCollection {#1558 …}
+children: []
-id: 32961
-titleTs: "'actual':4 'firewal':7 'need':5"
-bodyTs: "'1':34,103 '2':41,131 '3':51,189,230 '4':66,224 '5':77,102,248 '80':146,163 'abl':281 'access':223 'act':353 'action':318 'activ':337 'actor':340 'advoc':112 'along':28 'analog':363 'anoth':181 'answer':17,21,94,130 'anyth':320 'applic':213 'bad':339 'behaviour':198 'behind':74 'case':234 'communic':284 'comput':91 'could':199,302 'desir':109 'devic':62,205,244,310,316 'differ':174 'doesn':364 'done':202 'door':305,357,384 'essenti':126 'even':200 'exampl':148 'explicit':291 'expos':246 'extens':228 'extra':327 'feel':225 'find':14 'firewal':182,208,322 'follow':33 'forward':188 'front':356 'get':307,342 'go':151 'good':38,381 'grant':292 'group':241 'hole':155 'host':141 'hous':360,373 'instal':259 'know':270 'larger':240 'leav':104 'like':226,238,354 'line':30 'listen':214,376 'lot':106 'made':331 'major':19 'make':96,177,254,366 'malici':197 'matter':137 'mistak':330 'much':367 'nat':76,160 'need':43,53,68,79,184 'network':65 'non':129 'non-answ':128 'noth':221 'one':139,193,252 'open':165 'outsid':287 'peopl':344 'permiss':294 'poke':153 'port':145,162,169,187,217,379 'practic':40 'precaut':328 'prevent':338 'program':261,301 'provid':326 'public':172 'question':8 'rather':335 're':121 'readili':283 'router':158 'run':48,88 'satisfi':16 'search':6 'secur':39 'seem':324,345 'seen':25 'sens':98,256,368 'server':50,167 'servic':375 'softwar':87 'someth':27,115 'sort':195 'spent':3 'spi':313 'state':26 'strang':133,192 'think':117 'time':5 'treat':347 'trust':59,85,266 'unknown':300 'unless':289 'user':334 've':2 'want':277 'webserv':143 'without':116,371 'work':273 'world':288 'yet':12"
+cross: false
+upVotes: 0
+downVotes: 0
+ranking: 1706257325
+visibility: "visible "
+apId: "https://sh.itjust.works/post/13453975"
+editedAt: DateTimeImmutable @1728528893 {#1424
date: 2024-10-10 04:54:53.0 +02:00
}
+createdAt: DateTimeImmutable @1706170925 {#1415
date: 2024-01-25 09:22:05.0 +01:00
}
} |
|
Show voter details
|
| 13 |
DENIED
|
ROLE_ADMIN
|
null |
|
Show voter details
|
| 14 |
DENIED
|
ROLE_MODERATOR
|
null |
|
Show voter details
|